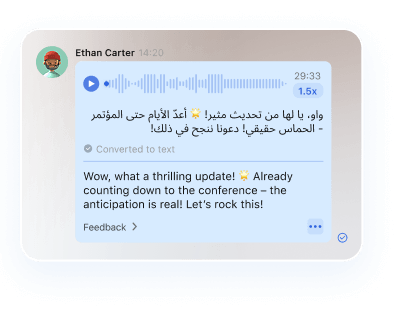
End-to-End Encrypted Sovereignty
End-to-End Encrypted Sovereignty
Messages, calls, and cabinet conferences with anti-eavesdropping, ensuring zero third-party access.
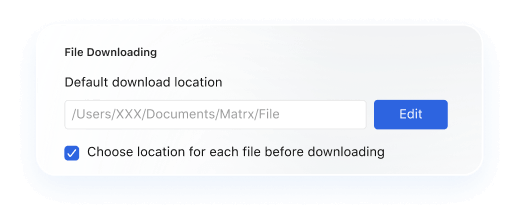
Sovereign Storage
Sovereign Storage
Recordings and files stored fragments; single-point leaks cannot compromise full datasets.
Dynamic File Protection
Dynamic File Protection
"One-time key" encryption for sensitive assets (e.g., policy drafts), preventing bulk decryption risks
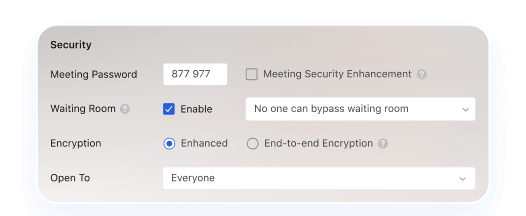
Department-Level Sandboxing
Department-Level Sandboxing
Space Data Isolation - Agency/project-specific encrypted workspaces.
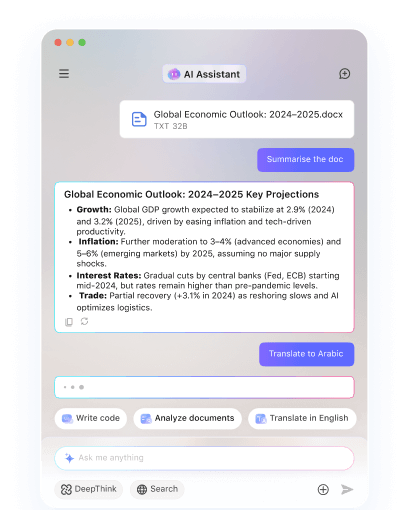
Sensitive File & Message Transfer
Sensitive File & Message Transfer
"View-Only" Mode - Restrict files to in-app preview (no download/forwarding).